 |
1 |  | 
Which of the following statements best describes what is meant by persistent data? |
|  | A) | Data that only exists while a program is running. |
|  | B) | Data in objects that keep trying to save themselves to disk storage. |
|  | C) | Data that must be stored after a program stops running and be available to other users. |
 |
 |
2 |  | 
Which of the following kinds of objects are used in an object-oriented system? |
|  | A) | Persistent objects only. |
|  | B) | Transient objects only. |
|  | C) | Both persistent and transient objects. |
 |
 |
3 |  | 
Which of the following is an example of a persistent object? |
|  | A) | A Client object in the Agate system. |
|  | B) | A ClientBroker object in the Agate system. |
|  | C) | A ClientProxy object in the Agate system. |
 |
 |
4 |  | 
Which of the following statements best describes how a database stores data? |
|  | A) | Relational databases store data in tables, and each table is a file. |
|  | B) | Databases provide a layer of abstraction between the way that data is presented to the user and the way that it is stored in files. |
|  | C) | Object databases store data in objects, and each object is a file. |
 |
 |
5 |  | 
Why might an object-oriented system use a relational DBMS? |
|  | A) | Many organizations have existing relational databases containing existing business data. |
|  | B) | Object databases are too complicated to use. |
|  | C) | Relational databases are inherently better than object databases for business applications. |
 |
 |
6 |  | 
Which of the following types of record structure is used in an XML file? |
|  | A) | Fixed length. |
|  | B) | Tagged. |
|  | C) | Header and detail. |
 |
 |
7 |  | 
Which of the following best describes a variable length record structure? |
|  | A) | Each record is made up of a number of fields, each of which has a fixed length in bytes. If the data in a field does not fill that many bytes, it is padded with a special character, usually null or space. |
|  | B) | Each record is made up of a number of fields, each of which may have a maximum length but has a minimum length of zero bytes. Either fields are separated by special delimiter characters or the length of each field is held in the record structure. |
|  | C) | Each record is tagged with a name in special characters. The end of the field is usually marked as well. Fields can contain other fields in complex nested structures. |
 |
 |
8 |  | 
Which of the following best describes a throwaway prototype? |
|  | A) | A throwaway prototype is discarded after it has been used to test out some aspect of the design. |
|  | B) | A throwaway prototype takes one sub-system and develops it across all the layers. |
|  | C) | A throwaway prototype is used to test the design of object deletion mechanisms. |
 |
 |
9 |  | 
Which of the following is a valid list of types of file organization? |
|  | A) | Tagged, serial and variable length. |
|  | B) | Hashed, index-sequential and serial. |
|  | C) | Serial, sequential and random. |
 |
 |
10 |  | 
Which of the following best describes serial file organization? |
|  | A) | Each record is written onto the end of the file. If a record is to be deleted, the file must be copied from the start to the deleted record, which is skipped, and written back to disk. |
|  | B) | Each record is written to file in a predetermined order, usually based on a key field. Records must be added in the right place in the file. |
|  | C) | Each record is located in the file by means of an algorithm that converts a key field into a position in the file. |
 |
 |
11 |  | 
Which of the following is a valid list of file access methods? |
|  | A) | Serial, index-sequential and direct. |
|  | B) | Serial, sequential and random. |
|  | C) | Tagged, serial and inverted. |
 |
 |
12 |  | 
Which of the following best describes index-sequential file access? |
|  | A) | Records are stored in blocks. The key of the record is used to calculate which block to store the data in, either using relative addressing or using a hashing algorithm. |
|  | B) | Records are stored in blocks. The key of the record is used to determine which block to store a record in. A block index is maintained, which lists the keys of the last record in each block. |
|  | C) | Records are stored in blocks. records are written into blocks in the order in which they are created. If there are too many records for the number of blocks, then the excess records are held in overflow blocks. |
 |
 |
13 |  | 
What is a hashing algorithm? |
|  | A) | 1. A way of padding data in fixed length fields with the ASCII hash character ‘#’ |
|  | B) | A way of separating fields in records using the ASCII has character ‘#’ as a delimiter. |
|  | C) | A way of converting record keys into numeric block addresses in a range of values. |
 |
 |
14 |  | 
Which of the following kinds of file would be used to store system settings? |
|  | A) | Parameter file. |
|  | B) | Temporary file. |
|  | C) | Master file. |
 |
 |
15 |  | 
Which of the following is not a disadvantage of using files to store data? |
|  | A) | As the number of applications grows, the number of files grows, and the same data may be held in different files, creating data integrity problems. |
|  | B) | Combining data from different applications to meet new business requirements is difficult, as data in different files may be accessed in different ways. |
|  | C) | Files can be used to hold prompts and labels in order to localize an application for use in different countries. |
 |
 |
16 |  | 
Which of the following is not a list of features of a database management system? |
|  | A) | DDL, DML, concurrency, tuning of storage. |
|  | B) | Integrity constraints, transaction management, security. |
|  | C) | DBA, DML, conceptual schema, security. |
 |
 |
17 |  | 
Which of the following is not an advantage of using a database management system? |
|  | A) | The use of a conceptual schema can eliminate unnecessary duplication of data. |
|  | B) | A database administrator must be employed to manage the system. |
|  | C) | The performance of the database can be tuned to optimise access to the data. |
 |
 |
18 |  | 
Which of the following statements is not true? |
|  | A) | Relational databases automatically convert objects into tables consisting of rows and columns. |
|  | B) | Relational databases hold data in two-dimensional tables that consist of rows and columns. |
|  | C) | Object databases hold objects as complex nested structures if necessary. |
 |
 |
19 |  | 
What is meant by normalization? |
|  | A) | Converting complex data structures into tables that meet clearly defined criteria. |
|  | B) | Removing dependencies from data in tables. |
|  | C) | Converting class diagrams into entity-relationship diagrams. |
 |
 |
20 |  | 
Which of the following is not a valid guideline for mapping classes to tables? |
|  | A) | Classes with simple data structures become tables. |
|  | B) | One-to-one associations are implemented using foreign key attributes. |
|  | C) | Collection classes are implemented using foreign key attributes. |
 |
 |
21 |  | 
Which of the following approaches is the best way of implementing inheritance in situations where it is known that the superclass is abstract? |
|  | A) | Only implement the superclass as a table. |
|  | B) | Only implement the subclasses as tables. |
|  | C) | Implement all the classes (superclasses and subclasses) as tables. |
 |
 |
22 |  | 
Which of the following statements best describes the use of object databases? |
|  | A) | Object databases store objects transparently. Compared to using a relational database, designing for an object database will have a minimal impact on the design of the system. |
|  | B) | Object databases store objects in relational database tables. The designer has to specify a set of rules for how the objects are to be mapped to the tables. |
|  | C) | Object databases provide the seamlessness claimed for object-oriented development by storing the operations of objects in the database, while the data is mapped to relational tables. |
 |
 |
23 |  | 
What is CORBA? |
|  | A) | A standard for passing messages between objects running on different machines. |
|  | B) | A standard for object-oriented databases. |
|  | C) | A misspelling of COBRA, the most popular beer among Indian software developers. |
 |
 |
24 |  | 
Which of the following statements best describes the use of the PersistentObject approach to designing the data storage layer? |
|  | A) | All objects in the system implement the PersistentObject interface. This interface acts as a broker between objects and the database. |
|  | B) | All the operations that are concerned with storing and retrieving objects from the database are implemented as class-scope operations. |
|  | C) | All classes in the system that represent persistent objects must inherit from an abstract superclass called PersistentObject that provides operations to store, delete and update objects in the database. |
 |
 |
25 |  | 
In the diagram below which operation is a class-scope operation? 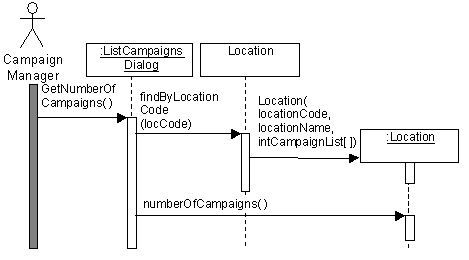 <a onClick="window.open('/olcweb/cgi/pluginpop.cgi?it=gif::Fig. 18.25::/sites/dl/free/0077098641/41598/ch18_q25_q.gif','popWin', 'width=519,height=330,resizable,scrollbars');" href="#"><img valign="absmiddle" height="16" width="16" border="0" src="/olcweb/styles/shared/linkicons/image.gif">Fig. 18.25 (50.0K)</a> <a onClick="window.open('/olcweb/cgi/pluginpop.cgi?it=gif::Fig. 18.25::/sites/dl/free/0077098641/41598/ch18_q25_q.gif','popWin', 'width=519,height=330,resizable,scrollbars');" href="#"><img valign="absmiddle" height="16" width="16" border="0" src="/olcweb/styles/shared/linkicons/image.gif">Fig. 18.25 (50.0K)</a>
Fig. 18.25
|
|  | A) | numberOfCampaigns(). |
|  | B) | findByLocationCode(). |
|  | C) | Location(). |
 |
 |
26 |  | 
Which of the following statements best describes the use of the broker framework? |
|  | A) | For each persistent class there is a broker class that is responsible for materializing instances of that class from the database and dematerialising them back into the database. |
|  | B) | Every persistent class inherits from the abstract RelationalBroker class, which provides the mechanisms for storing and retrieving object instances. |
|  | C) | For every persistent object there is a broker object that is responsible for materializing the object from the database and dematerialising it back into the database. |
 |
 |
27 |  | 
Why might six caches be used in a persistence framework? |
|  | A) | Six caches are better than one. |
|  | B) | To distinguish between the different states of objects (new/old and clean/dirty/deleted). |
|  | C) | The magic number seven plus or minus two. |
 |
 |
28 |  | 
In the diagram below, what is the purpose of the IntCampaignProxy class? 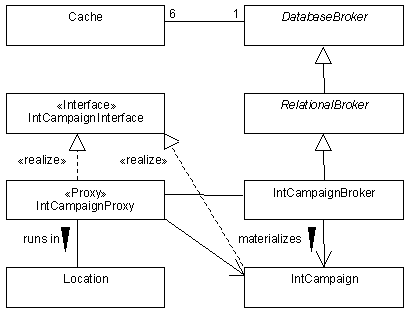 <a onClick="window.open('/olcweb/cgi/pluginpop.cgi?it=gif::Fig. 18.28::/sites/dl/free/0077098641/41598/ch18_q28_q.gif','popWin', 'width=460,height=386,resizable,scrollbars');" href="#"><img valign="absmiddle" height="16" width="16" border="0" src="/olcweb/styles/shared/linkicons/image.gif">Fig. 18.28 (50.0K)</a> <a onClick="window.open('/olcweb/cgi/pluginpop.cgi?it=gif::Fig. 18.28::/sites/dl/free/0077098641/41598/ch18_q28_q.gif','popWin', 'width=460,height=386,resizable,scrollbars');" href="#"><img valign="absmiddle" height="16" width="16" border="0" src="/olcweb/styles/shared/linkicons/image.gif">Fig. 18.28 (50.0K)</a>
Fig. 18.28
|
|  | A) | The IntCampaignProxy contains the IntCampaignBroker object. |
|  | B) | The IntCampaignProxy decouples the IntCampaign from the cache. |
|  | C) | The IntCampaignProxy acts as a placeholder for the actual IntCampaign. The IntCampaign is only materialized from the database when required. |
 |



 2002 A McGraw-Hill Online Learning Centre
2002 A McGraw-Hill Online Learning Centre